Protecting your software from cyber threats is more critical than ever. Cyber attacks can lead to stolen data, operational disruptions, and significant financial losses. For businesses and individuals, ensuring robust software security is a necessary step toward safeguarding sensitive information and maintaining trust.
Understanding the Growing Threat
Cyber threats are becoming increasingly sophisticated, targeting software vulnerabilities through methods like ransomware, phishing, and Distributed Denial-of-Service (DDoS) attacks. A staggering number of data breaches, resulting in over 22 billion exposed records globally in recent years, highlights the urgency of addressing these challenges.
To combat these threats, organizations must adopt a proactive and strategic approach to secure their software systems. Here are some effective strategies to help protect your software from cyber threats.
Strengthen Authentication Mechanisms

The foundation of software security begins with robust authentication measures. Multi-factor authentication (MFA) adds multiple layers of verification, making it harder for unauthorized users to gain access. Combining elements like passwords, biometrics, and security tokens ensures maximum protection.
Tips for Effective Authentication:
- Use strong, unique passwords that include letters, numbers, and special characters.
- Avoid reusing passwords for different accounts or platforms.
- Regularly update passwords and disable inactive accounts.
- Implement Single Sign-On (SSO) solutions for easier and centralized access management.
Keep Software Updated with Regular Patches

Hackers often exploit vulnerabilities in outdated software. Ensuring your software is regularly updated and patched can close security loopholes and prevent breaches.
Best Practices for Updating Software:
- Automate software updates to avoid delays.
- Maintain a list of all software and regularly check for updates.
- Test patches in a safe environment before full deployment.
- Monitor vendor notifications for news about potential vulnerabilities.
Conduct Code Reviews and Security Testing
Secure software development begins with clean and error-free code. Regular code reviews and vulnerability testing can identify security risks early in the process. Automated tools like static and dynamic application security testing (SAST/DAST) are essential for scanning vulnerabilities.
Secure Coding Guidelines:
- Follow industry standards such as OWASP for secure coding practices.
- Avoid embedding sensitive information, like API keys, directly in the code.
- Use secure queries to prevent SQL injection.
- Rely on well-maintained libraries and frameworks.
Encrypt Sensitive Data
Encryption is a powerful tool for protecting data from unauthorized access. Encrypting data ensures that even if it is intercepted, it remains unreadable without the appropriate decryption keys.
Key Encryption Steps:
- Use strong encryption standards like AES-256 for data storage.
- Protect data in transit using protocols such as TLS.
- Regularly update and securely store encryption keys.
- Comply with encryption regulations relevant to your industry.
Secure Development Life Cycle (SDLC)
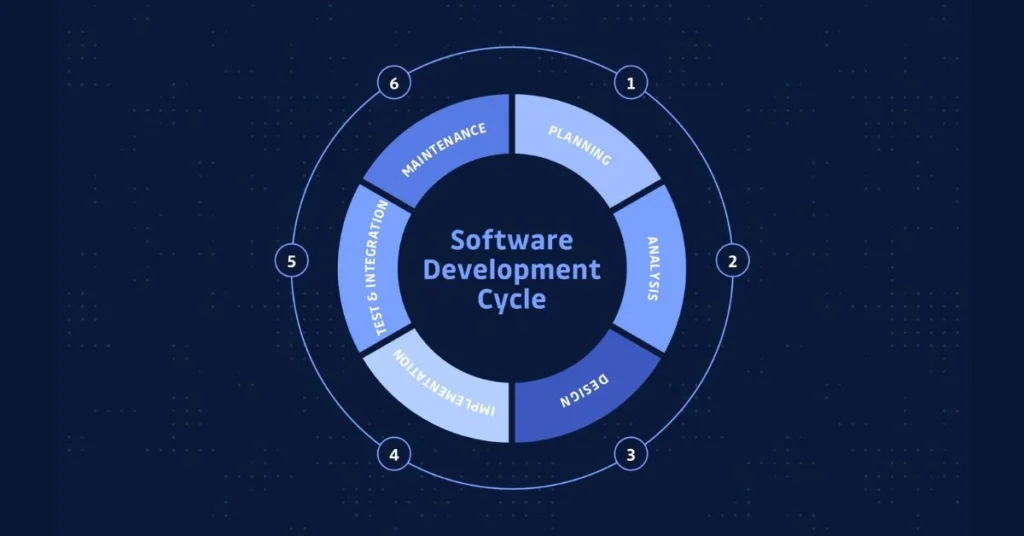
Integrating security at every stage of the Software Development Life Cycle (SDLC) ensures vulnerabilities are addressed proactively. This approach embeds security into the foundation of your software.
Essential SDLC Practices:
- Perform threat modeling during the design phase to identify potential risks.
- Train developers in secure coding and cybersecurity practices.
- Use automated testing tools to monitor security throughout development.
- Implement DevSecOps to merge security with CI/CD pipelines.
Educate Employees on Cybersecurity
Human error is a major cause of cyber incidents. Educating employees on cybersecurity best practices helps minimize the risk of accidental breaches.
Key Training Topics:
- Identifying phishing attempts and social engineering tactics.
- Properly handling sensitive data and credentials.
- Reporting suspicious activities without delay.
- Keeping software and systems up to date.
Employ Advanced Security Tools
Modern tools powered by AI and machine learning can identify and mitigate threats in real time. Tools like firewalls, intrusion detection systems, and endpoint security solutions strengthen your overall defense.
Recommended Tools:
- Security Information and Event Management (SIEM) systems for monitoring.
- Antivirus and anti-malware software to prevent infections.
- Penetration testing tools to identify weak points.
- Threat intelligence platforms for staying ahead of emerging risks.
Monitor and Audit Continuously
Continuous monitoring and auditing are crucial to identifying and addressing threats promptly. Regular checks and alerts ensure vulnerabilities are detected and resolved.
Monitoring Best Practices:
- Set up alerts for suspicious activity.
- Conduct regular audits to assess security performance.
- Maintain detailed logs for analysis in case of breaches.
- Use centralized systems for easier tracking and oversight.
Develop a Backup and Recovery Plan

Despite the best precautions, breaches can still occur. A solid backup and disaster recovery plan ensures your data is safe and operations can be restored quickly.
Backup Strategy:
- Follow the 3-2-1 rule: three copies of your data, stored on two different media, with one off-site.
- Encrypt backup data to keep it secure.
- Regularly test the recovery process.
- Create clear documentation and practice recovery scenarios.
Build a Security-Focused Culture
Creating a culture of security ensures every team member takes cybersecurity seriously. Security awareness should be a shared responsibility across the organization.
Ways to Promote Security Awareness:
- Encourage employees to report vulnerabilities without fear of repercussions.
- Recognize and reward proactive security efforts.
- Make cybersecurity a regular topic in meetings and training sessions.
- Update and communicate security policies frequently.
Conclusion
Securing your software from cyber threats requires a combination of technology, vigilance, and cultural awareness. By implementing strong authentication, regular updates, secure coding practices, and continuous monitoring, you can build a robust defense against cybercriminals. Empowering employees and fostering a security-first mindset further ensures your systems remain resilient in an ever-evolving threat landscape.
Taking these steps not only protects your software but also safeguards your organization’s reputation and user trust. Start strengthening your defenses today to stay ahead in the fight against cyber threats.
FAQs:
1. What are the most common cyber threats to software?
The most common cyber threats include phishing attacks, ransom ware, malware, SQL injection, and Distributed Denial-of-Service (DDoS) attacks. These threats exploit software vulnerabilities to steal data or disrupt operations.
2. How often should I update my software?
You should update your software as soon as updates or security patches are released. Automating updates can help ensure timely application without delays.
3. Why is encryption important for software security?
Encryption protects sensitive data by converting it into an unreadable format, making it accessible only to authorized users with decryption keys. This ensures data remains secure even if intercepted.
4. What is a secure software development life cycle (SDLC)?
A secure SDLC integrates security practices into every phase of software development, from design to deployment. This approach helps identify and mitigate risks early in the process.
5. How can employees help prevent cyber threats?
Employees can prevent cyber threats by following best practices, such as using strong passwords, identifying phishing attempts, handling sensitive information securely, and promptly reporting suspicious activities.
Discover how SaaS platforms can revolutionize your business operations with cutting-edge solutions—explore more at NoderSoft’s SaaS Platforms.

